‘Insidious’ client-side malware targets banks through customers
Banks are at risk from a new kind of ‘client side injected malware’ attack, in which attackers install malware on the customer’s device and use it as a base to attack their bank as well as steal private information.
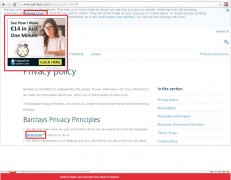
While man-in-the-browser attacks using injected ads, spyware scripts, unauthorised cookies and fake surveys designed to look like they are part of the bank’s website or app have been around for some time, the CSIM attack is a relatively new malware phenomenon which has grown rapidly in the last six months.
Online security company Namogoo estimates that out of the 89 million people in the US who used banking services via mobile phone last year, between 5 and 13 million of these were infected with CSIM malware. This represents an infection rate between 5% and 15%.
One of the most striking features of the CSIM attack is that because it exists solely on the consumer’s browser or device, banks may find it difficult to monitor and control.
“What many financial institutions don’t understand is that even though the malware lives on a consumer’s device, it can cause a bank to be in breach of their own privacy standards, or even worse, in non-compliance with banking laws designed to protect the customer,” said co-founder and COO Ohad Greenshpan. “Just because you can’t see it on your servers doesn’t mean it’s not attacking your website or mobile app. While you’re watching your server back doors, this new form of malware is freely entering through the new front door – the customer’s computer, smartphone or browser.”
Consumers themselves fall victim to CSIM mainly through three paths, according to Namogoo’s research into CSIM:
- Free utility apps and browser extensions that secretly bundle in malicious software, such as free flashlights, keyboards and free screensavers
- Unprotected routers – consumers regularly change Wi-Fi passwords but very often forget to even set the router login
- Legitimate consumer security software and popular anti-virus products that surreptitiously download ad injectors and CSIM onto consumer devices
The company also found that CSIM increased from 5% to 20% infection rate among iOS users – a finding that it attributes to the mistaken belief that Macs and iPhones are more secure than other devices. When CSIM is installed on a user device, it runs malicious scripts that steal the user’s credentials and send sensitive data to the script owner.
Tell-tale signs of a CSIM infection include ads, product recommendations and content that would not normally be present on a banking app or website. Namagoo’s report suggests that consumers may blame the bank for the poor user experience created by this additional content, adding a reputational and user experience element to the problem. Another common method is a survey which appears to be legitimate, but is actually just a device to steal the consumer’s personal information. It is also worth being aware that if a router ‘s login credentials are compromised, all devices accessing that router’s Wi-Fi will be infected with CSIM – so it’s worth changing your router login every now and then.
Namogoo created a technology aimed at combatting CSIM attacks. It is designed to suppress all active CSIM on consumer’s computer or browser when that consumer visits a Namogoo-protected site. The company does this by sending malware injection blocking rule sets to these websites.
“This is the new frontier for malware,” said Greenshpan. “It’s insidious, it’s alarmingly intelligent and it’s coming through the path of least resistance – via innocent consumers who don’t even know they’re infected. If financial institutions expect to keep winning the malware wars, they need to come to the new frontline.”
Cyber security continues to be rated as the single largest fear of bank executives, according to a recent study published by the DTCC in May. Among others, recent cyber crime incidents include the discovery earlier this year of an online gang using the Carbanak malware which stole up to $1 billion from banks in 30 countries around the world in a series of highly-sophisticated attacks over the last two years; and the events of February 2015, when a joint international operation by Europol’s European Cybercrime Centre seized servers said to have controlled the Ramnit botnet that had infected 3.2 million computers internationally.