Don’t click this link: how authID aims to protect you from yourself
Picture this: you’re in Las Vegas for Money20/20 2022. As CEO, you’re representing your firm at the conference, looking to make an impact and generate new business leads. Your phone alerts you to an e-mail from the organisers inviting you backstage for an opportunity to meet some of the stars visiting the conference. All looks legit. You confirm your attendance and think nothing more of it. When’s lunch?
However, it turns out this email was a targeted phishing attack, aimed at C-level execs and sent out by identity authentication firm authID.
Out of 436 opens, 210 recipients – 48% – clicked the simulated phishing link embedded in the email. Recipients included CCOs, CTOs, CISOs, CIOs, and heads of fraud and risk for the largest banks in the US.
The human factor
AuthID provides secure identity authentication through its Human Factor Authentication (HFA) platform Verified, which combines FIDO2 passwordless device authentication with cloud biometrics to “authenticate the human behind the device”.

AuthID CEO Tom Thimot
“Powered by sophisticated biometric and artificial intelligence technologies, our technology eliminates passwords to fortify enterprise security and trust between organisations, employees, and customers,” authID CEO Tom Thimot tells FinTech Futures.
AuthID leverages the “human factor” and facial recognition technology to remediate today’s social engineering attacks. “If the human element is the problem in 82% of breaches, then solving for the human element — with cloud biometrics — is the ideal solution,” Thimot adds.
The firm operates across the financial services, healthcare, and cybersecurity markets, as it believes these sectors are more comfortable and familiar with passwordless authentication and are the industry segments that can benefit the most from HFA.
“With highly valued assets and data, these segments are frequently targeted by social engineering and account compromise attacks that can cause significant damage to reputation, positioning, and market trust,” Thimot says.
Gone phishin’
The main weapon in a cybercriminal’s arsenal is the use of phishing – links that lead to a webpage that impersonates a brand, enticing you to click on them by saying your account is locked, suggesting your payment information is out of date or missing, or that you need to log in to retrieve a message or important document.
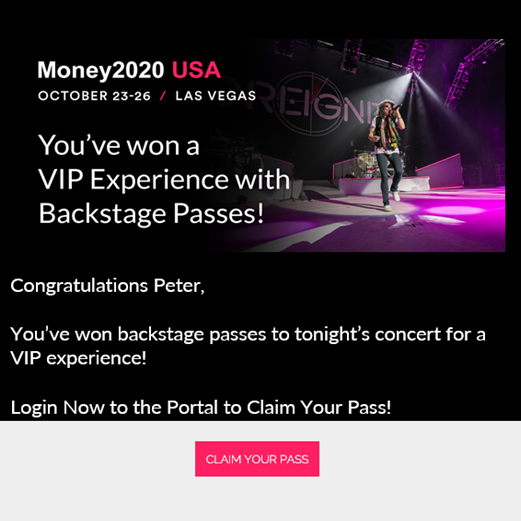
AuthID’s Money20/20 USA phishing email
“The purpose is to get a victim to hand over sensitive information or download malware,” Thimot explains. Attacks rely on deception and a sense of urgency, with misspelled URLS, site redirects, and unknown or suspicious message sources acting as major red flags.
Phishing can take the form of general, mass-market emails which are sent to millions of potential victims to try to trick them into logging in to fake versions of popular websites. SMS messages can also be utilised in a similar fashion.
Spear phishing comprises more targeted attacks focused on a specific individual, while ‘whaling’ attacks are aimed at the biggest fish — CEOs or other high-value targets like company board members.
Others may fall prey to business email compromise (BEC), in which attackers pretend to be a company CEO or other top executive, typically to get other individuals in that organisation to transfer money.
0000
Passwords, as a form of cybersecurity, have been around for 60 years and their application is fraught with issues. They are ripe for disruption, and Thimot believes we are “in the midst of a fundamental evolution in the science of authentication”, backed by a concerted effort to replace “frustrating and insecure” credentials with cryptographic FIDO2 passkeys, or a FIDO token bound to a device.
“Social engineering attacks exploiting multi-factor authentication (MFA) technology have been successful in compromising major enterprises this year, including Twilio, Cisco, and Intuit,” Thimot says.
Out of 4,110 breaches studied in the 2022 Verizon Data Breach Investigations Report (DBIR), compromised credentials due to insider error were the root cause of 82% breaches. On top of this, 84% of financial institutions also experienced account takeovers in the past year.
“Legacy MFA places assumed trust in the recipient of a code, knowledge of the user, or holder of a device, making these methods easily phished and vulnerable to bad actors as they do not really authenticate the user behind the device,” Thimot explains.
Because most device-based authenticators do not require “live” biometrics for user identity and access authentication, they are highly susceptible to a variety of fraudulent activities which can provide bad actors with unauthorised access to enterprise systems — “often with catastrophic consequences”.
Incredibly, Thimot says that most legacy MFA tech doesn’t meet the current minimum standards promulgated by the US government for zero trust architecture. The US Office of Management and Budget (OMB) noted that agencies must use strong MFA that is enforced at the application layer, not just the network layer, and that phishing-resistant MFA is required for agencies and their partners.
Biometrics and deepfakes
AuthID views biometrics as the future of cybersecurity. “Biometrics eliminate any identity assumptions, validate the identity of the user, and verify the true account owner whenever increased assurance is needed,” Thimot explains.

Biometrics are key to a passwordless future
The firm focuses its solutions on facial biometrics thanks to the worldwide adoption of mobile devices and the advancements of desktop computers with cameras. Facial biometrics can be easily performed and analysed with a simple act of a user taking a selfie on any device, at any time.
But does the use of facial biometrics open up the possibility that bad actors will exploit deepfake tech to crack cybersecurity in the future?
Presentation attacks occur when fraudsters attempt to attack a biometric system by creating spoofs or fakes that are then presented to the biometric sensors. Such spoofs or deepfakes can use a printed photo, an image or video of a person on a tablet, 3D masks, models, or other forms of impersonation.
Thimot says the firm’s Verified platform leverages AI and Presentation Attack Detection technology to detect these attacks through passive liveness challenges on the user’s facial image.
Verified’s passive liveness process captures images from a user’s mobile phone camera or desktop webcam and analyses them against several quality metrics. These frames are then sent through a pipeline of multiple presentation attack detection algorithms to detect spoofing attempts. The aggregate scores of these processes are returned by the system to indicate whether a biometric sample is authentic and should be considered for facial verification.
“In the future, we will move toward being multi-modal with authentication – that is, using multiple biometrics combined with other factors,” Thimot says, with biometrics set to be used more and more for in-person transactions, for everything from in-store transactions to gaining access to a restricted building.
AuthID intends to bring biometrics to common workflows that are plagued with identity challenges, such as account recovery, re-authentication during high-risk transactions, and authentication for shared devices.
“Shared mobile devices are one of the hottest growing markets, but organisations are running into adoption issues due to poor login experiences on these devices. We are helping to bolster adoption through our portable authentication workflows.”
Protect yourself
If the top minds of our industry can fall victim to a phishing attack, what hope do the rest of us have?
In a world where multi-tasking is the norm, Thimot says, anyone can be caught off guard. So, what can you do to avoid being phished? It’s important to stay diligent and review things carefully before you hand over any personal information.
Slowing down, carefully reading the email or text, and identifying warning signs may prevent a successful attack. Learn common phishing techniques and obvious indicators of a phishing attempt.
Being aware of red flags – for instance, grammar or spelling errors, a sense of urgency, requests for personal information, or inconsistent email addresses – can help you spot them in real life.
Check link destinations and verify the sender before clicking on any link. Hovering over or long pressing a link will reveal the true destination.
Lastly, make contact with the sender to validate that the email or text is legitimate. Be sure to use known contact information, such as the business phone number from their website.










































